Scope –
Create Three VRFs for Three separate clients
Create a Shared VRF
Leak routes from each VRF to the Shared_VRF
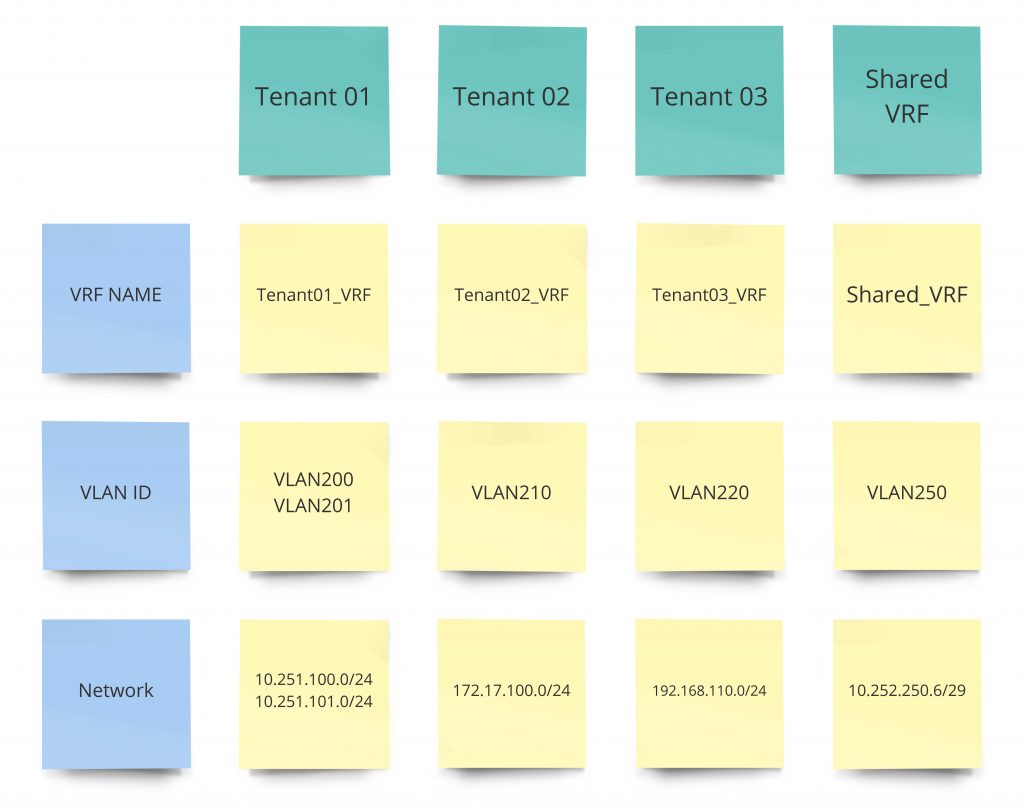
Logical overview
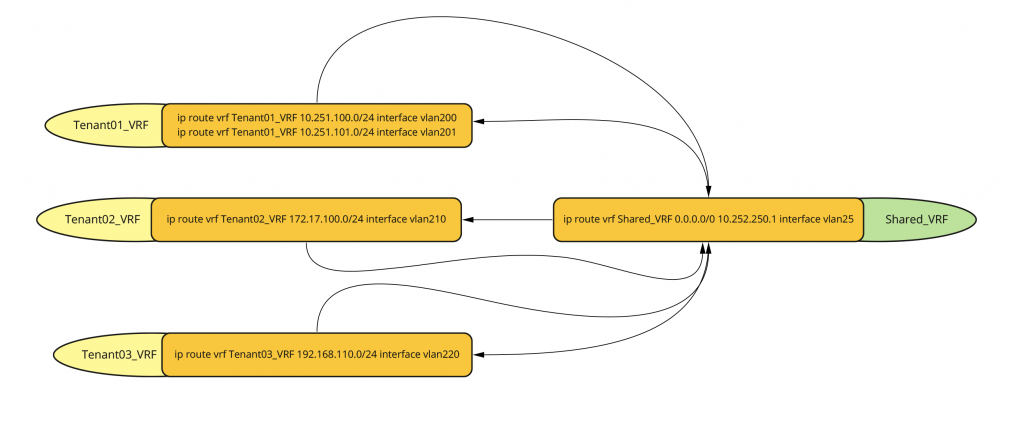
Create the VRFs
ip vrf Tenant01_VRF
ip vrf Tenant02_VRF
ip vrf Tenant03_VRF
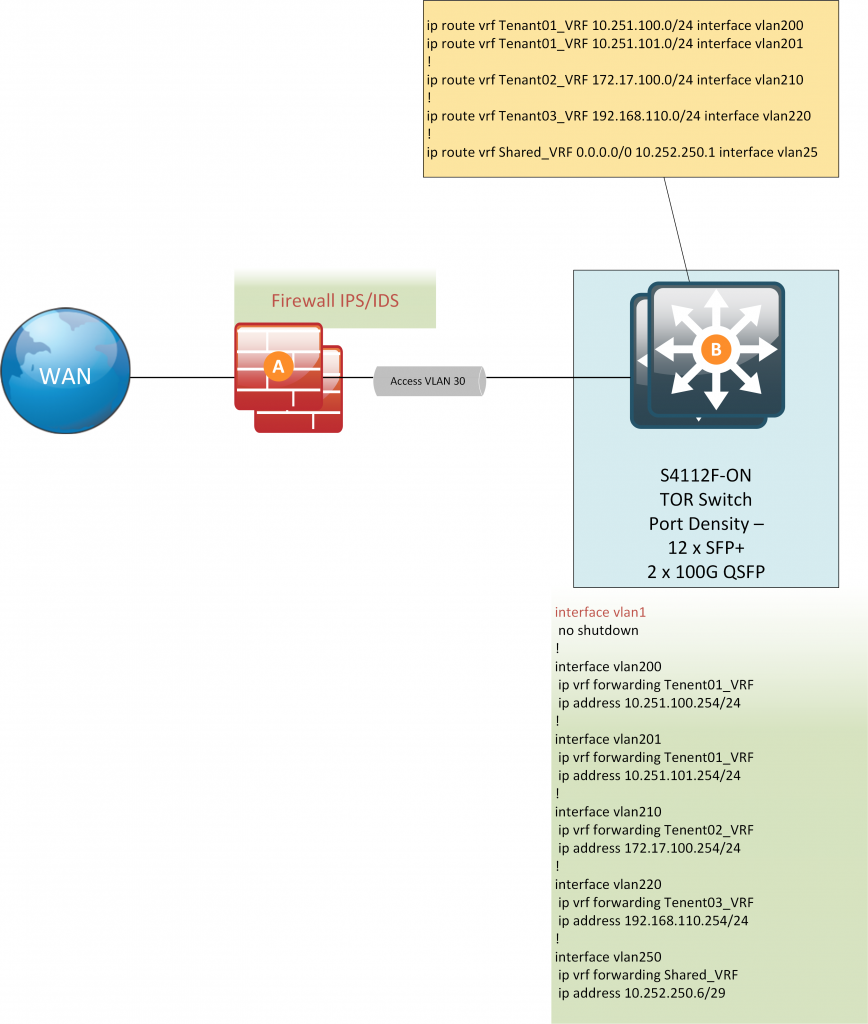
Create and initialize the Interfaces (SVI, Layer 3 interface, Loopback)
We are creating Layer 3 SVIs Per tenant
interface vlan200
mode L3
description Tenant01_NET01
no shutdown
ip vrf forwarding Tenant01_VRF
ip address 10.251.100.254/24
!
interface vlan201
mode L3
description Tenant01_NET02
no shutdown
ip vrf forwarding Tenant01_VRF
ip address 10.251.101.254/24
!
interface vlan210
mode L3
description Tenant02_NET01
no shutdown
ip vrf forwarding Tenant02_VRF
ip address 172.17.100.254/24
!
interface vlan220
no ip address
description Tenant03_NET01
no shutdown
ip vrf forwarding Tenant03_VRF
ip address 192.168.110.254/24
!
interface vlan250
mode L3
description OSPF_Routing
no shutdown
ip vrf forwarding Shared_VRF
ip address 10.252.250.6/29
Confirmation
LABCORE# show i
image interface inventory ip ipv6 iscsi
LABCORE# show ip interface brief
Interface Name IP-Address OK Method Status Protocol
=========================================================================================
Vlan 200 10.251.100.254/24 YES manual up up
Vlan 201 10.251.101.254/24 YES manual up up
Vlan 210 172.17.100.254/24 YES manual up up
Vlan 220 192.168.110.254/24 YES manual up up
Vlan 250 10.252.250.6/29 YES manual up up
LABCORE# show ip vrf
VRF-Name Interfaces
Shared_VRF Vlan250
Tenant01_VRF Vlan200-201
Tenant02_VRF Vlan210
Tenant03_VRF Vlan220
default Vlan1
management Mgmt1/1/1
Route leaking
For this Example we are going to Leak routes from each of these tenant VRFs in to the Shared VRF
This design will allow each VLAN within the VRFs to see each other, which can be a security issue how ever you can easily control this by
- narrowing the routes down to hosts
- Using Access-lists (not the most ideal but if you have a playbook you can program this in with out any issues)
Real world use cases may differ use this as a template on how to leak routes with in VRFs, update your config as needed
Create the route export statements wihtin the VRFS
ip vrf Shared_VRF
ip route-import 2:100
ip route-import 3:100
ip route-import 4:100
ip route-export 1:100
ip vrf Tenant01_VRF
ip route-export 2:100
ip route-import 1:100
ip vrf Tenant02_VRF
ip route-export 3:100
ip route-import 1:100
ip vrf Tenant03_VRF
ip route-export 4:100
ip route-import 1:100
Lets Explain this a bit
ip vrf Shared_VRF
ip route-import 2:100 -----------> Import Leaked routes from target 2:100
ip route-import 3:100 -----------> Import Leaked routes from target 3:100
ip route-import 4:100 -----------> Import Leaked routes from target 4:100
ip route-export 1:100 -----------> Export routes to target 1:100
if you need to filter out who can import the routes you need to use the route-map with prefixes to filter it out
Setup static routes per VRF as needed
ip route vrf Tenant01_VRF 10.251.100.0/24 interface vlan200
ip route vrf Tenant01_VRF 10.251.101.0/24 interface vlan201
!
ip route vrf Tenant02_VRF 172.17.100.0/24 interface vlan210
!
ip route vrf Tenant03_VRF 192.168.110.0/24 interface vlan220
!
ip route vrf Shared_VRF 0.0.0.0/0 10.252.250.1 interface vlan25
- Now these static routes will be leaked and learned by the shared VRF
- the Default route on the Shared VRF will be learned downstream by the tenant VRFs
- instead of the default route on the shared VRF, if you scope it to a certain IP or a subnet you can prevent the traffic routing between the VRFs via the Shared VRF
- if you need routes directly leaked between Tenents use the ip route-import on the VRF as needed
Confirmation
Routes are being distributed via internal BGP process
LABCORE# show ip route vrf Tenant01_VRF
Codes: C - connected
S - static
B - BGP, IN - internal BGP, EX - external BGP, EV - EVPN BGP
O - OSPF, IA - OSPF inter area, N1 - OSPF NSSA external type 1,
N2 - OSPF NSSA external type 2, E1 - OSPF external type 1,
E2 - OSPF external type 2, * - candidate default,
+ - summary route, > - non-active route
Gateway of last resort is via 10.252.250.1 to network 0.0.0.0
Destination Gateway Dist/Metric Last Change
----------------------------------------------------------------------------------------------------------
*B IN 0.0.0.0/0 via 10.252.250.1 200/0 12:17:42
C 10.251.100.0/24 via 10.251.100.254 vlan200 0/0 12:43:46
C 10.251.101.0/24 via 10.251.101.254 vlan201 0/0 12:43:46
LABCORE#
LABCORE# show ip route vrf Tenant02_VRF
Codes: C - connected
S - static
B - BGP, IN - internal BGP, EX - external BGP, EV - EVPN BGP
O - OSPF, IA - OSPF inter area, N1 - OSPF NSSA external type 1,
N2 - OSPF NSSA external type 2, E1 - OSPF external type 1,
E2 - OSPF external type 2, * - candidate default,
+ - summary route, > - non-active route
Gateway of last resort is via 10.252.250.1 to network 0.0.0.0
Destination Gateway Dist/Metric Last Change
----------------------------------------------------------------------------------------------------------
*B IN 0.0.0.0/0 via 10.252.250.1 200/0 12:17:45
C 172.17.100.0/24 via 172.17.100.254 vlan210 0/0 12:43:49
LABCORE#
LABCORE# show ip route vrf Tenant03_VRF
Codes: C - connected
S - static
B - BGP, IN - internal BGP, EX - external BGP, EV - EVPN BGP
O - OSPF, IA - OSPF inter area, N1 - OSPF NSSA external type 1,
N2 - OSPF NSSA external type 2, E1 - OSPF external type 1,
E2 - OSPF external type 2, * - candidate default,
+ - summary route, > - non-active route
Gateway of last resort is via 10.252.250.1 to network 0.0.0.0
Destination Gateway Dist/Metric Last Change
----------------------------------------------------------------------------------------------------------
*B IN 0.0.0.0/0 via 10.252.250.1 200/0 12:17:48
C 192.168.110.0/24 via 192.168.110.254 vlan220 0/0 12:43:52
LABCORE# show ip route vrf Shared_VRF
Codes: C - connected
S - static
B - BGP, IN - internal BGP, EX - external BGP, EV - EVPN BGP
O - OSPF, IA - OSPF inter area, N1 - OSPF NSSA external type 1,
N2 - OSPF NSSA external type 2, E1 - OSPF external type 1,
E2 - OSPF external type 2, * - candidate default,
+ - summary route, > - non-active route
Gateway of last resort is via 10.252.250.1 to network 0.0.0.0
Destination Gateway Dist/Metric Last Change
----------------------------------------------------------------------------------------------------------
*S 0.0.0.0/0 via 10.252.250.1 vlan250 1/0 12:21:33
B IN 10.251.100.0/24 Direct,Tenant01_VRF vlan200 200/0 09:01:28
B IN 10.251.101.0/24 Direct,Tenant01_VRF vlan201 200/0 09:01:28
C 10.252.250.0/29 via 10.252.250.6 vlan250 0/0 12:42:53
B IN 172.17.100.0/24 Direct,Tenant02_VRF vlan210 200/0 09:01:28
B IN 192.168.110.0/24 Direct,Tenant03_VRF vlan220 200/0 09:02:09
We can ping outside to the internet from the VRF IPs
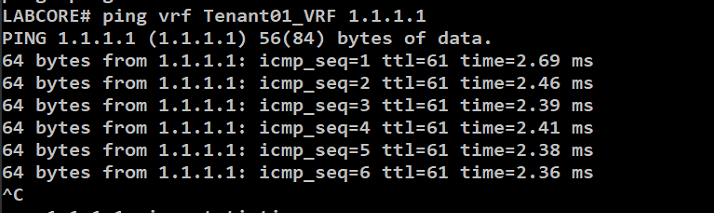
Redistribute leaked routes via IGP
You can use a Internal BGP process to pickup routes from any VRF and redistribute them to other IGP processes as needed – Check the Article for that information